commercebuild currently does not offer two-factor/multi-factor authentication (2FA/MFA) or single sign-on (SSO). However, there is an alternative way to implement 2FA for a specific number of users using Cloudflare and their Workers. In this guide, we'll show you how you can implement it.
Note that this guidance is mainly for users who would access any URIs containing /admin. In its current form, it will not be suitable for general web store users/shoppers, although a developer may be able to adapt this guidance so that it can be applied to a broader set of users.
Additionally, this guidance assumes that your company has signed up for Cloudflare and uses Cloudflare to host its DNS. Not sure if your web store uses Cloudflare? Go to DNS Checker, select "NS" (name servers) from the dropdown menu, type the naked domain, and click "Search". If the name servers that appear have "cloudflare.com" in them, then your company is using Cloudflare.
Video Tutorial
The following video covers this entire article:
Generate A Secret
In order to properly test and implement this guidance, you will need a mechanism to generate base32 encoded secrets. For the purposes of this documentation, you can use this JavaScript to generate a token as well as the accompanying QR code.
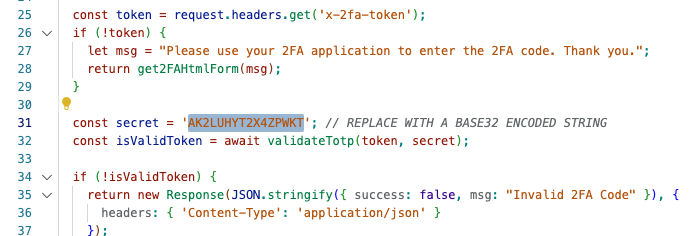
Once you have your secret and you've added it to your Authenticator app (we prefer Google Authenticator), which will look something like AK2LUHYT2X4ZPWKT, then you're ready for the next step.
Create a Worker at Cloudflare
Next, you will need to login to the Cloudflare Dashboard and create a Cloudflare Worker. Please see our guidance on the creation of Cloudflare Workers. Please also refer to Cloudflare's documentation on Workers.
You will need to use this script for your Worker.
Before you "Save and deploy" your worker, be sure that you update the secret constant with the value you've generated. For the purposes of this documentation, you'd need to change the secret to AK2LUHYT2X4ZPWKT:
Add the Route for the Worker
In the final step, you will need to add your newly-created Worker to a route. Specifically, we want this worker to run on all requests to URLs including /admin. Please see our guidance on the creation of routes for Cloudflare Workers.
To achieve this, our Route will be our webstore domain, followed by /admin*, and our Worker will be 2fa, which we've created in the previous step:
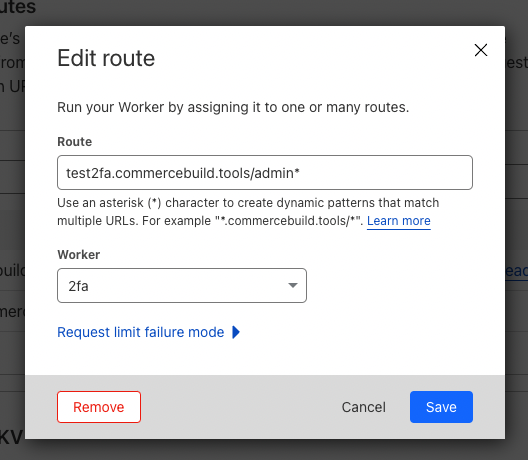
Once you've made these adjustments, be sure to click "Save."
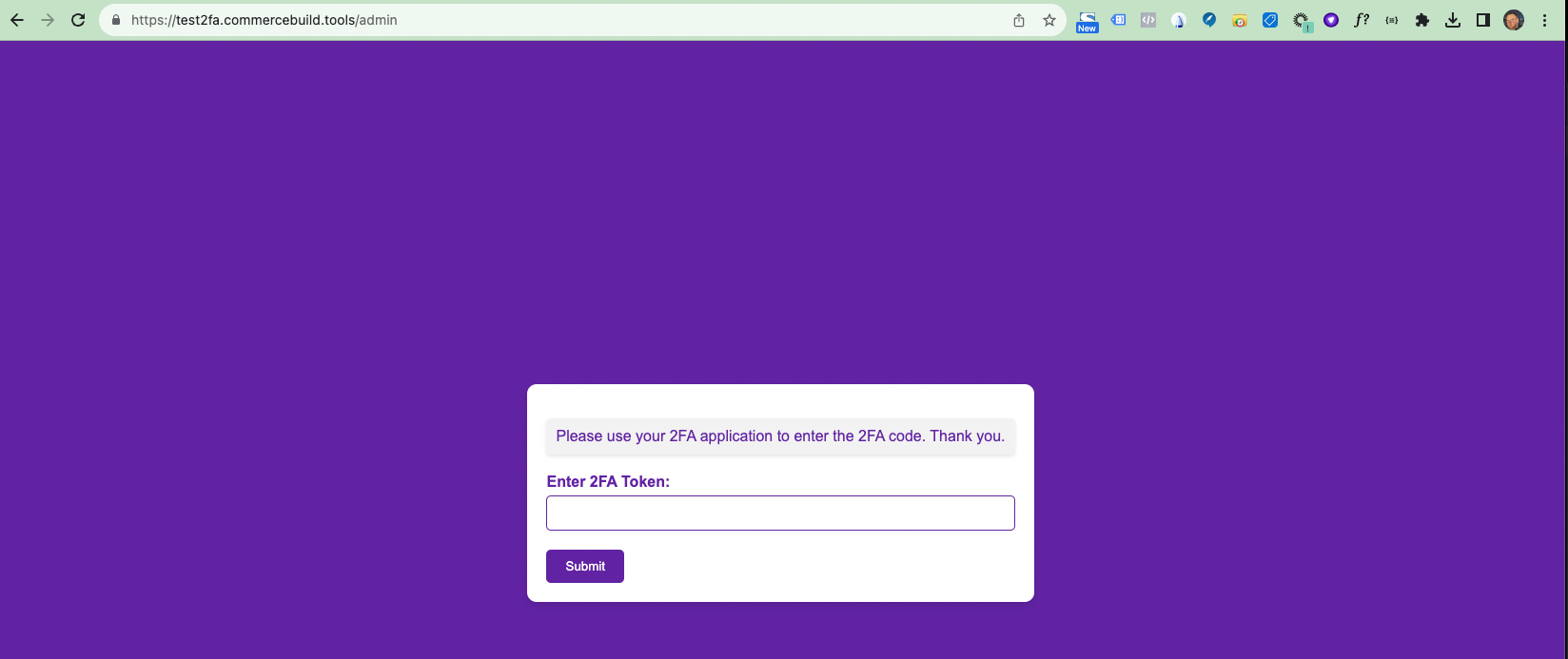
Testing 2FA
Now, when I visit the Route above, I see the 2FA form required to access the page:
Frequently Asked Questions:
I can still see the login page, even though I haven't entered a 2FA code yet. Why?
The Worker in question is not tied to the webstore login (i.e. /user/login/ ), and this is by design for the purposes of this documentation. Ordinary, non-administrator web store users need to be able to sign in without being prompted for a 2FA code. This worker only prevents the /admin pages from being accessed if the 2FA code has not been correctly entered.
How does Cloudflare "remember" that the Cloudflare token has been entered correctly?
The Worker caches the user IP address via Cloudflare Cache for a period of an hour. If an IP has been previously authorized and an hour has not passed, then any user connecting from that IP will be able to access an admin page without being prompted for a 2FA code.
How frequently will an admin user need to re-enter their 2FA code with this Worker?
It's currently set to request a 2FA code after an hour, regardless of activity. You can modify the script to accommodate any time period you prefer.
Can we add multiple secrets for different users?
Currently, the script does not support this. However, a JavaScript developer should be able to assist with required modifications to support multiple secrets.
Which authenticator apps are supported?
Testing has only been conducted with Google Authenticator. Any apps supporting secrets for Google Authenticator should work as well.