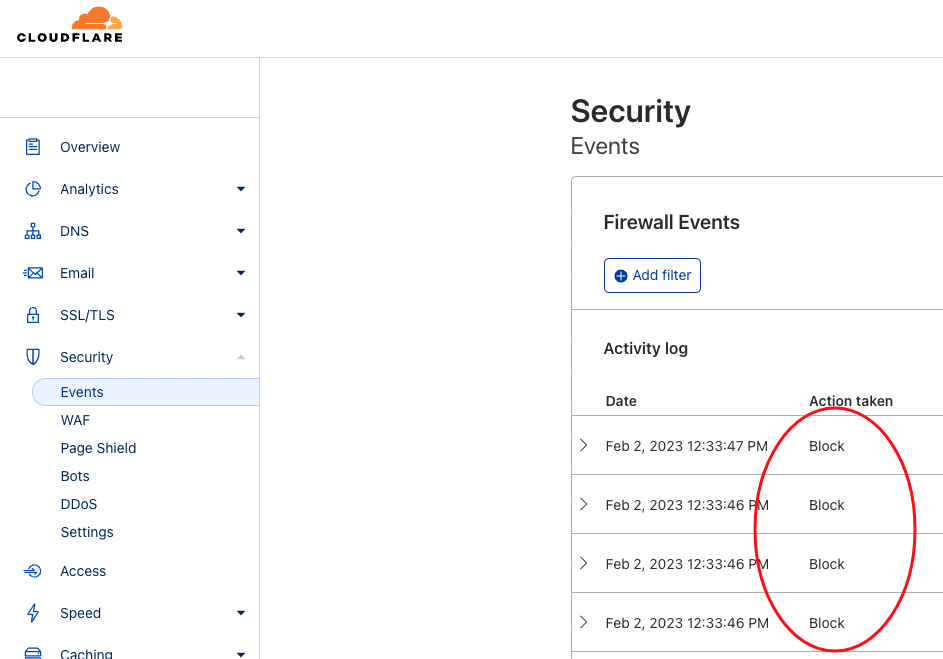
In addition to Cloudflare's firewall rules, their rate limiting can also be effective at increasing your web store's security. Note that Cloudflare rate limiting is not free, but it is very affordable if it is used on a limited, targeted basis.
For example, if you wish to use rate limiting, we might recommend it for the URL that processes web store payments, i.e. *.mywebstore.com/checkout/onepage/place_order*.
You can enable Google reCAPTCHA on your payment pages by going to System > Features > B2C (Public) and toggling Enable Captcha at Checkout. reCAPTCHA is excellent, but not infallible.
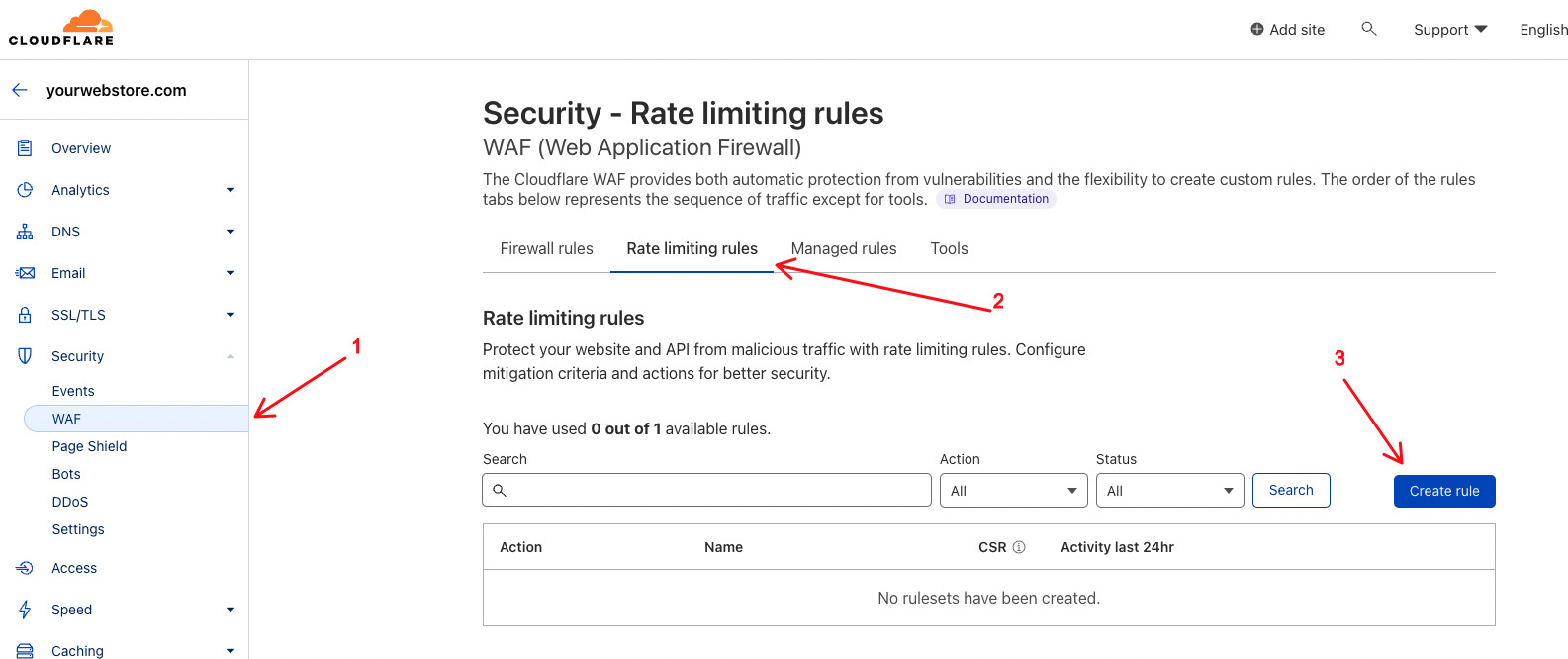
Create a Custom Rate Limiting Rule
To get started, navigate to the Security section in your Cloudflare dashboard, click WAF, then Rate limiting rules and finally click Create rule.
Configure the Rate Limiting Rule
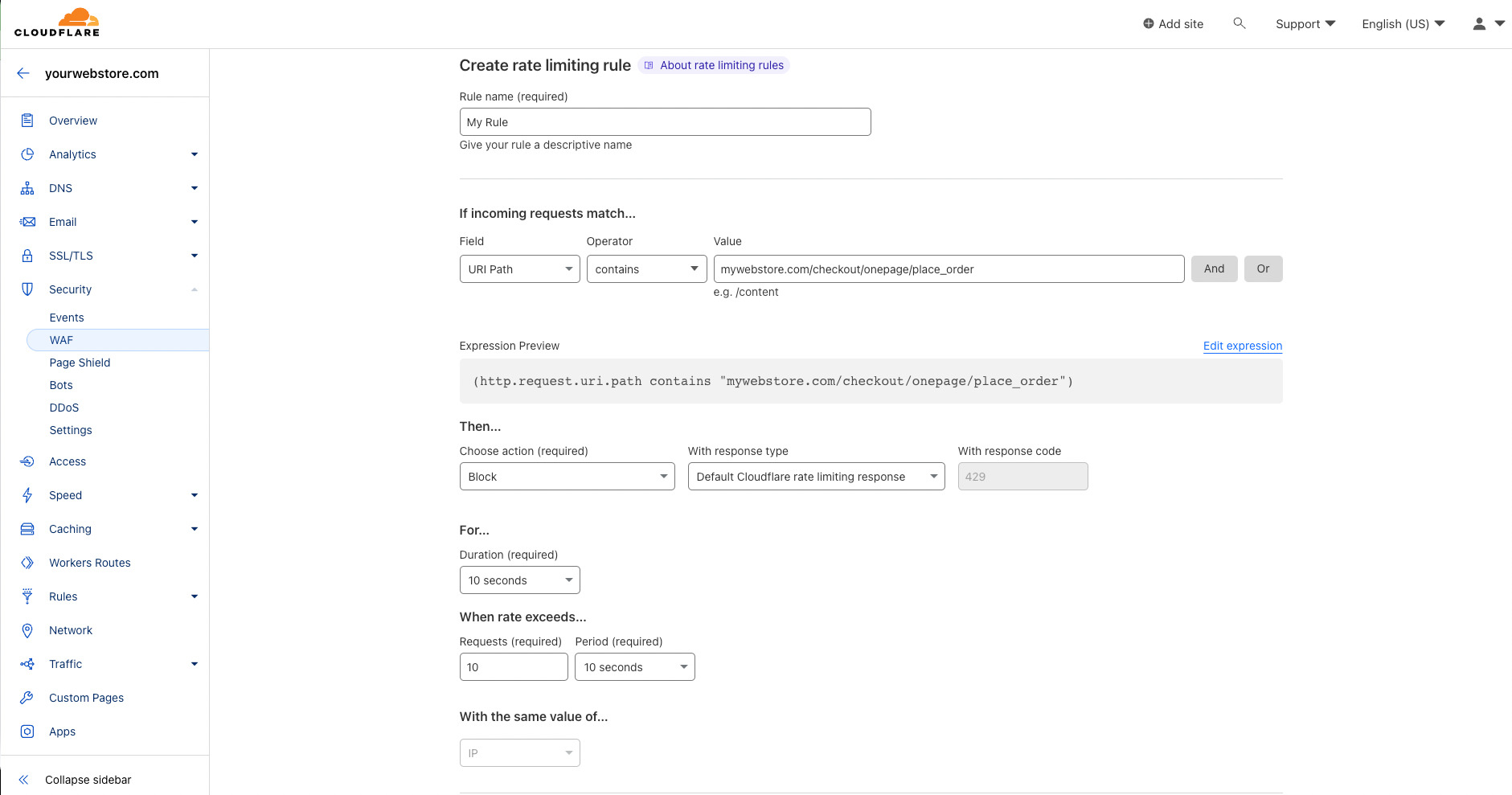
- Give your rule a name. This should be memorable in case you need to modify this rule in the future.
- For example, copy-paste
mywebstore.com/checkout/onepage/place_order(or use any part of another URL that you'd like), but modify it so thatmywebstore.comis replaced with your domain name. If you set the operator tocontains, then any URL that contains the value will be affected by this rule. - Next, you want to decide the action. Here we have it set to block the request for 10 seconds when there are more than 10 requests in a 10 second period from the same IP address.
- Save your changes and deploy the rate limiting rule.
Verifying the Rule
If you visit the URL more than 10 times in your browser in less than 10 seconds, you should trigger the rule.
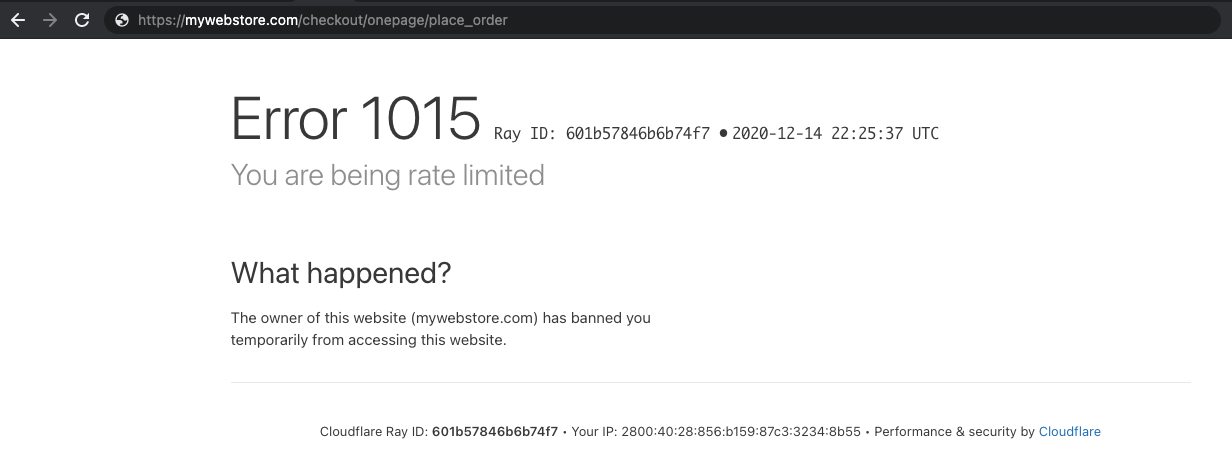
Additionally, you can monitor which IPs are being rate limited in the Events log by going to Security > Events